Android users have been alerted about a wide range of applications which can be downloaded from the Google Play Store.
Reportedly, these applications have been hit by malware. The massive invasive Italian spyware campaign was being hosted for two years!
This was first identified by non-profit security organization Security Without Borders (SWB). SWB shares that the campaign was utilizing Italian-language service applications from mobile operators apps that instead of doing their stated function are in fact spyware.
As the apps were targeting Italian citizens, they were decoying local services and were downloaded by a couple of hundreds each.
Which applications have been impacted?
The report further shares that not only is this spyware capable of copying a user’s data, but also has the ability to extract user information from applications.
This includes data collected by Viber messenger app data, WhatsApp logs, Wi-Fi passwords, the WeChat data, GPS coordinates of the phone (live), Facebook Messenger conversations, address book, Facebook contacts list, calls log, Calendar events, Gmail information, and cellular tower information.
Furthermore, the malware is also being said to be able to record phone calls, retrieve browsing history and bookmarks from Chrome, and record ambient audio using the device’s microphone.
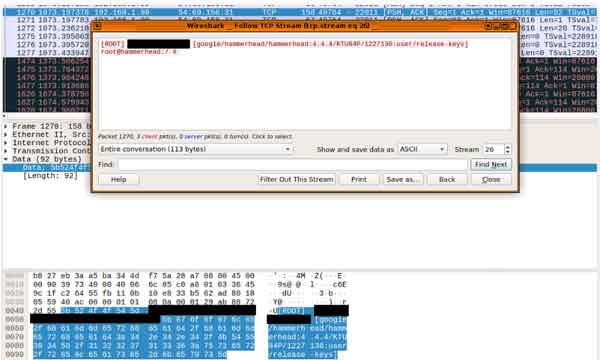
The stolen data is temporarily stored on the device’s SD card for eventual downloading by the command and control server.
Exodus- What it does & how does it work
Being called ‘Exodus’, the malware was existing since 2016, however, after coming under notice, Google has since then removed the applications causing the trouble.
Nonetheless, the malicious actors behind the campaign have been known to re-establish them on Google Play. Google confirmed to SWB that about 25 variants of Exodus have been found and removed.
The Exodus malware triggers right after being downloaded, it grabs the device’s basic info, such as the phone number, to validate the target and then dynamically loads and execute the primary stage 2 payload.
“We identified previously unknown spyware apps being successfully uploaded on Google Play Store multiple times over the course of over two years. These apps would remain available on the Play Store for months and would eventually be re-uploaded,” the researchers wrote.
“Of the various binaries downloaded, the most interesting is null, which serves as a local and reverse shell, and rootdaemon, which takes care of privilege escalation and data acquisition. rootdaemon will first attempt to jailbreak the device using a modified version of the DirtyCow exploit,” the report stated.
Legal and law enforcement experts told Motherboard the spyware could be illegal. “These apps would remain available on the Play Store for months and would eventually be re-uploaded.”
Where did it come from?
All the evidence collected by Security Without Borders in its investigation indicates the malware was developed by eSurv, an Italian company based in the southern city of Catanzaro, in the Calabria region.
Stay tuned to Brandsynario for more news and updates.










































